jasypt dubbo配置密文存放使用详解
目录
- jasypt进行密码密文存放
- jasypt使用
- 与Dubbo联用
jasypt进行密码密文存放
许多项目里会对配置文件中的敏高文件进行加密处理,避免了信息泄露问题。在springboot项目里,可以通过引入jasypt进行密码密文存放
jasypt使用
1.引入jasypt-spring-boot-starter包
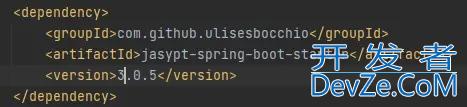
2.配置信息
jasypt:
encryptor:
algorithm: PBEWithHMACSHA512AndAES_256
password: 123456 //salt
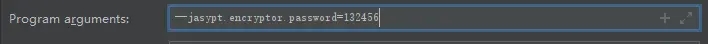
或将password放在启动行参数里
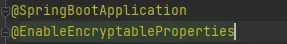
3.启动项添加注解
4.生成密文
可以通过网上的密码工具生成,也可以使用jasypt生成
AES256TextEncryptor stringEncryptor = new AES256TextEncryptor();
stringEncryptor.setPassword("123456"); //salt
String encrypt = stringEncryptor.encrypt("test"); //加密 test为你的密码
String decrypt = stringEncryptor.decrypt(encrypt); //解密
5.将生成的encrypt放到原来的密码处并用ENC()包裹即可,ENC()可通过jasypt.encryptor.algorithm.property.prefix/suffix进行配置
test: ENC(sdjflskdjfsjdflksdjalfjdslkfjksdjfkldsjkfsf) //此处放上面生成的encrypt
jasypt:
encryptor:
algorithm: PBEWithHMACSHA512AndAES_256
property:
prefix: #默认为ENC(
suffix: #默认为)
与Dubbo联用
它会存在一个问题,就是无法对dubbo的配置进行加密,解决方法如下:
将下面文件添加到项目里,目前仅支持PBEWithHMACSHA512AndAES_256,如需要支持其他,可自行在TODO处添加处理逻辑
//JasyptPreparedEnvListener.Java
package com.demo.listener;
import org.jasypt.util.text.AES256TextEncryptor;
import org.springframework.boot.context.event.ApplicationEnvironmentPreparedEvent;
import org.springframework.context.ApplicationListener;
import org.springframework.context.annotation.Configuration;
import org.springframework.core.env.PropertySource;
import org.springframework.web.context.support.StandardServletEnvironment;
import java.util.Iterator;
import java.util.Map;
/**
* use jasypt to decrypt the data
*/
@Configuration
public class JasyptPreparedEnvListener implements ApplicationListener<ApplicationEnvironmentPreparedEvent> {
private String getSalt(StandardServletEnvironment env ){
String salt = env.getProperty("jasypt.encryptor.password");
if(salt == null || salt.isBlank()) {
rjseturn null;
}
return salt;
}
private String getConfigPrefix(StandardServletEnvironment env ){
String rst = env.getPropertfnHqXMIy("jasypt编程客栈.encryptor.property.config.prefix");
if(rst == null || rst.isBlank()) {
return "CONFIG_ENC(";
}
return rst;
}
private String getConfigSuffix(StandardServletEnvironment env ){
String rst = env.getProperty("jasypt.encryptor.property.config.suffix");
if(rst == null || rst.isBlank()) {
return ")";
}
return rst;
}
private boolean isEncrypted(String value,String prefix,String suffix){
if(value == null || value.isBlank()){
return false;
}
String trimValue = value.trim();
return trimValue.startsWith(prefix) && trimValue.endsWith(suffix);
}
private String unwrapEncryptedValue(String value,String prefix,String suffix){
return value.substring(prefix.length(),value.length() - suffix.length());
}
private String getAlgorithm(StandardServletEnvironment env){
String rst = env.getProperty("jasypt.encryptor.algorithm");
if(rst == null || rst.isBlank()) {
return "PBEWithHMACSHA512AndAES_256";
}
return rst;
}
private Object getDecryptor(StandardServletEnvironment env){
String algorithm = getAlgorithm(env);
Object obj = null;
if(algorithm.equals("PBEWithHMACSHA512AndAES_256")){
String salt = getSalt(env);
if(salt != null){
obj = new AES256TextEncryptor();
((AES256TextEncryptor)obj).setPassword(salt);
}
}//TODO add other decryptor logic here
return obj;
}
private String decrypt(StandardServletEnvironment env,Object decryptpr,String value){
String algorithm = getAlgorithm(env);
if(algorithm.equals("PBEWithHMACSHA512AndAES_256")){
AES256TextEncryptor aes256TextEncryptor = (AES256TextEncryptor)decryptpr;
try{
return aes256TextEncryptor.decrypt(value);
}catch (Exception e){
System.out.println("decrypt failed: " + e);
return value;
}
} //TODO add other decryptor logic here
return value;
}
@Override
public void onApplicationEvent(ApplicationEnvironmentPreparedEvent event) {
StandardServletEnvironment env =(StandardServletEnvironment) event.getEnvironment();
// 1. get decryptor
Object decryptor = getDecryptor(env);
if(decryptor == null){
retuandroidrn;
}
String configPrefix = getConfigPrefix(env);
String configSuffix = getConfigSuffix(env);
// 2. loop property
Iterator<PropertySource<?>> iterator = env.getPropertySources().iterator();
while (iterator.hasNext()) {
PropertySource<?> source = iterator.next();
String name = source.getName();
if (name.startsWith("applicationConfig")) {
Object o = source.getSource();
if (o instanceof Map) {
for (Map.Entry<String, Object> entry : ((Map<String, Object>) o).entrySet()) {
String key = entry.getKhttp://www.devze.comey();
String value = env.getProperty(key);
if (isEncrypted(value, configPrefix, configSuffix)) {
//3.解密
String newValue = decrypt(env, decryptor, unwrapEncryptedValue(value, configPrefix, configSuffix));
System.setProperty(key, newValue);
}
}
}
}
}
}
}
- 在resources资源文件夹下新增META-INF/spring.factories,添加以下内容 或在main函数启动里通过addListener api进行添加
org.springframework.context.ApplicationListener = com.demo.listener.JasyptPreparedEnvListener
将需要密文存储的地方使用CONFIG_ENC()包裹即可,CONFIG_ENC也可配置
jasypt:
encryptor:
algorithm: PBEWithHMACSHA512AndAES_256
property:
config:
prefix: #默认为CONFIG_ENC(
suffix: #默认为)
它的思路就是在Springboot的ApplicationEnvironmentPreparedEvent事件里对配置文件信息进行处理
ApplicationEnvironmentPreparedEvent: spring boot 对应Enviroment已经准备完毕,但此时上下文context还没有创建。在该监听中获取到ConfigurableEnvironment后可以对配置信息做操作,例如:修改默认的配置信息,增加额外的配置信息等等
以上就是jasypt dubbo配置密文存放使用详解的详细内容,更多关于jasypt dubbo配置密文存放的资料请关注编程客栈(www.devze.com)其它相关文章!


 加载中,请稍侯......
加载中,请稍侯......
精彩评论