Python实现IP端口扫描程序
完整代码
#javascript!/usr/bin/env python
# -*- coding: utf-8 -*-
"""
IP端口扫描程序
输入IP地址,扫描该IP哪些端口对外是开放的,输出端口列表
"""
import socket
import sys
import concurrent.futures
import ipaddress
from tabulate import tabulate
import time
def is_valid_ip(ip):
"""
验证IP地址是否有效
"LpEXzmRE""
try:
ipaddress.ip_address(ip)
return True
except ValueError:
return False
def scan_port(ip, port, timeout=1):
"""
扫描单个端口是否开放
参数:
ip (str): 目标IP地址
port (int): 要扫描的端口
timeout (float): 连接超时时间(秒)
返回:
bool: 如果端口开放返回True,否则返回False
"""
try:
# 创建TCP套接字
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(timeout)
# 尝试连接
result = sock.connect_ex((ip, port))
# 关闭套接字
sock.close()
# 如果连接成功,端口是开放的
return result == 0
except (socket.error, socket.timeout, OSError):
return False
def scan_ports(ip, port_range=None, max_workers=100):
"""
扫描IP地址的多个端口
参数:
ip (str): 目标IP地址
port_range (tuple): 端口范围,格式为(起始端口, 结束端口)
max_workers (int): 最大并发线程数
返回:
list: 开放端口列表
"""
if port_range is Nowww.devze.comne:
# 默认扫描常见端口
port_range = (1, 1024)
start_port, end_port = port_range
open_ports = []
total_ports = end_port - start_port + 1
print(f"开始扫描 {ip} 的端口 {start_port}-{end_port}...")
start_time = time.time()
# 使用线程池进行并发扫描
with concurrent.futures.ThreadPoolExecutor(max_workers=max_workers) as executor:
# 创建扫描任务
future_to_port = {
executor.submit(scan_port, ip, port): port
for port in range(start_port, end_port + 1)
}
# 处理完成的任务
completed = 0
for future in concurrent.futures.as_completed(future_to_port):
port = future_to_port[future]
completed += 1
# 显示进度
if completed % 100 == 0 or completed == total_ports:
progress = (completed / total_ports) * 100
elapsed = time.time() - start_time
print(f"进度: {completed}/{total_ports} ({progress:.1f}%) - 已用时间: {elapsed:.1f}秒", end="\r")
try:
if future.result():
open_ports.append(port)
print(f"\n发现开放端口: {port}")
except Exception as e:
print(f"\n扫描端口 {port} 时出错: {e}")
print(f"\n扫描完成! 总用时: {time.time() - start_time:.1f}秒")
return open_ports
def display_open_ports(ip, open_ports):
"""
显示开放端口列表
"""
if not open_ports:
print(f"\n{ip} 没有发现开放的端口")
return
# 尝试获取常见端口的服务名称
port_info = []
for port in sorted(open_ports):
try:
service = socket.getservbyport(port)
except (socket.error, OSError):
service = "未知"
port_info.append([port, service])
# 显示表格
print(f"\n{ip} 的开放端口:")
headers = ["端口", "可能的服务"]
print(tabulate(port_info, headers=headers, tablefmt="grid"))
LpEXzmRE
def main():
"""
主函数
"""
# 获取用户输入
if len(sys.argv) > 1:
target_ip = sys.argv[1]
else:
target_ip = input("请输入要扫描的IP地址: ")
# 验证IP地址
if not is_valid_ip(target_ip):
print(f"错误: '{target_ip}' 不是有效的IP地址")
sys.exit(1)
# 获取端口范围
try:
custom_range = input("请输入要扫描的端口范围 (格式: 起始端口-结束端口) [默认: 1-1024]: ")
if custom_range:
start, end = map(int, custom_range.split('-'))
if start < 1 or end > 65535 or start > end:
raise ValueError
port_range = (start, end)
else:
port_range = (1, 1024)
except ValueError:
print("错误: 无效的端口范围,使用默认范围 1-1024")
port_range = (1, 1024)
# 扫描端口
open_ports = scan_ports(target_ip, port_range)
# 显示结果
display_open_ports(target_ip, open_ports)
if __name__ == "__main__":
try:
main()
except KeyboardInterrupt:
print("\n\n扫描被用户中断")
sys.exit(0)
except Exception as e:
print(f"\n程序执行出错: {e}")
sys.exit(1)
结果如下
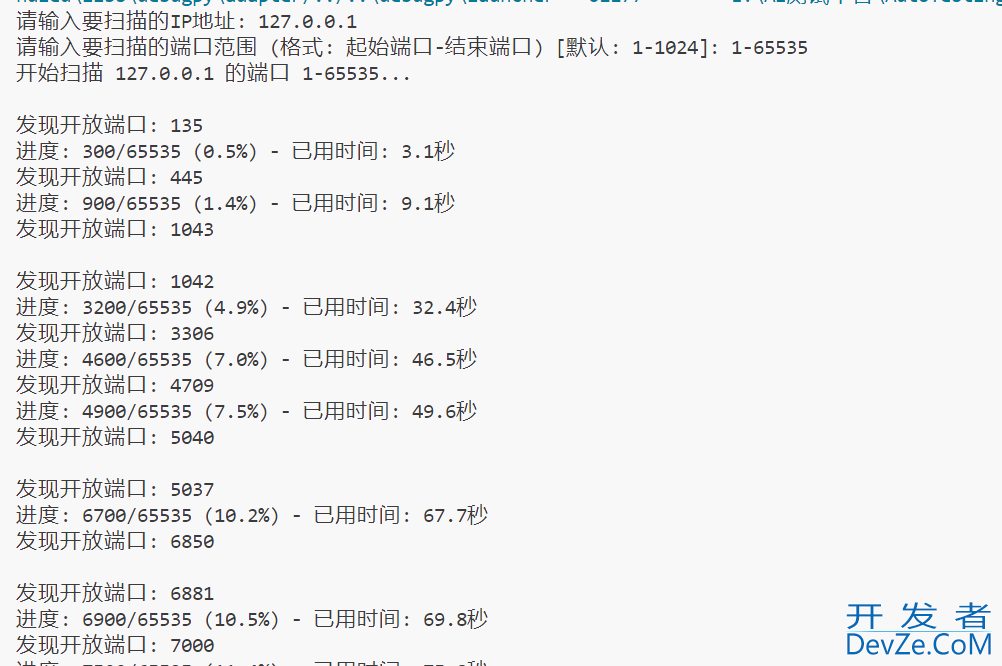
方法补充
python批量扫描ip端口
该程序的主要功能如下:
1. 从自有API接口获取所有的外网IP段;
2. 用Nmap 遍历扫描所有的IP段,-oX 生成XML的扫描报告;
3. 用xml.etree.ElementTree模块方法读取XML文件,将ip,开放端口,对应服务等写入mysql数据库。
功能很简单,没有满足老大高大上的需求,所以这个小项目就这么英勇的挂掉了!~~~完全都还没考虑程序异常终止,扫描服务器异常歇菜的情况。
贴上代码:
#coding:utf-8
import sys,os,time,subprocess
import MySQLdb
import re,urllib2
import ConfigParser
from IPy import IP
import xml.etree.ElementTree as ET
nowtime = time.strftime('%Y-%m-%d',time.localtime(time.time()))
configpath=r'c:portscanconfig.ini'
#传入api接口主路径,遍历获取所有的ip列表,用IPy模块格式成127.0.0.1/24的格式
def getiplist(ipinf):
serverarea=['tj101','tj103','dh','dx']
iplist=[]
for area in serverarea:
ipapi=urllib2.urlopen(ipinf+area).read()
for ip in ipapi.split('n'):
#判断如果ip列表不为空,转换成ip/网关格式,再格式化成ip/24的格式
if ip:
ip=ip.replace('_','/')
ip=(IP(ip))
iplist.append(str(ip))
ipscan(iplist,nmapathx)
#传递ip地址文件和nmap路径
def ipscan(iplist,nmapath):
#古老的去重,对ip文件中的ip地址进行去重
newiplist=[]
scaniplist=[]
for ip in iplist:
if ip not in newiplist:
newiplist.append(ip)
#遍历所有ip段,批量扫描,生成xml格式报告
for ip in newiplist:
filename=nowtime+ip.split('/')[0]+'.xml'
filepath=r"c:portscanscanres\"
nmapcmd=nmapath+' -PT '+ip.strip('rn')+' -oX '+filepath+filename
os.system(nmapcmd)
scaniplist.append(ip)
writeinmysql(scaniplist)
#入库模块是某大婶发写好的给我 我只是简单修javascript改了哈,主要是xml.etree.ElementTree模块。
def writeinmysql(scaniplist):
filepath=r"c:portscanscanres"
for ip in scaniplist:
xmlfile=filepath+'\'+ip+'.xml'
#缩进哈 发文章的时候临时改的,懒得缩进了
root=ET.parse(xmlfile).getroot()
allhost=root.findall('host')
conn=MySQLdb.connect(host='10.5.10.57',user='nxadmin',passwd='nxadmin.com',port=3306,db='scandb',charset='utf8')
cur= conn.cursor()
for host in allhost:
address = host.find('address')
#首先判断端口是不是open的,如果是再进行入库
for port in host.find('ports').findall('port'):
if port.find('state').attrib['state']=="open":
ip=address.attrib['addr']
portval=port.attrib['portid']
state=port.find('state').attrib['state']
sql = "INSERT INTO portscan (ip,port,state) VALUES(%s,%s,%s)"
params=[ip,portval,state]
cur.execute(sql,params)
conn.commit()
cur.close()
conn.close()
if __name__=="__main__":
#读取配置文件中要扫描的IP apiurl和nmap安装文件路径
config=ConfigParser.ConfigParser()
config.readfp(open(configpath,'rb'))
nmapathx=config.get('nmap','nmapath')
ipinf=config.get('ip','ipinf')
getiplist(ipinf)
配置文件c:portscanconfig.ini中主要是api接口主url,nmap安装路径。
python 使用 scapy 扫描内网IP或端口
1.利用ICMP协议探测内网IP
def ping_ip(ip_fex):
# 扫描范围: 128~254
for i in range(128, 255):
ip = f'{ip_fex}.{i}'
print(f'\r{ip}', end='')
output = os.popen(f'ping -n 1 -w 100 {ip} | findstr TTL=').read()
if len(output) > 0:
print(f"\n{ip} online")
if __name__ == '__main__':
ping_ip('192.168.110')
2.利用ARP协议探测内网IP
def ip_thread(start, ip_fex):
for i in range(start, start + 20):
ip = f'{ip_fex}.{i}' # 目标ip
try:
pkg = ARP(psrc=f'{ip_fex}.1', pdst=ip) # 伪造ARP广播
reply = sr1(pkg, timeout=1, verbose=False) # 发送ARP并获取响应包
if reply:
print(f'\n{ip}->{reply[ARP].hwsrc}') # 显示MAC地址
else:
print(f'\r{ip} ...', end='')
except Exception as e:
print(e)
def ip_scan(ip_fex):
# 关闭警告
import logging
logging.getLogger("scapy.runtime").setLevel(logging.ERROR)
# 端口范围 1~254
for i in range(1, 255, 20):
threading.Thread(target=ip_thread, args=(i, ip_fex)).start()
3.利用TCP协议探测端口
端口信息在TCP层, 可以使用TCP协议数据包探测端口是否开放
伪造 SYN 数据包, 根据响应数据中的标志位 flags 来判断端口是否正常响应.
SYN: 0x002
ACK: 0x010SYN-ACK: 0x012
def scan_port(ip):
for port in range(22, 100):
try:
pkg = IP(src='192.168.112.123', dst=ip) / TCP(dport=port, flags='S')
reply = sr1(pkg, timeout=1, verbose=False)
if reply:
if reply[TCP].flags == 0x12: # SYN-ACK
print(f'port->[{port}]')
except Exception as e:
print(e)
到此这篇关于Python实现IP端口扫描程序的文章就介绍到这了,更多相关Python IP端口扫描内容请搜索编程客栈(www.devze.com)以前的文章或继续浏览下面的相关文章希望大家以后多多支持编程客栈(www.devze.com)!



 加载中,请稍侯......
加载中,请稍侯......
精彩评论