Mobile Phone Authorization System Question
I have a difficult to nail down/solve problem.
I am creating a system that has two parties: The User wants to perform and authorize an action , and the second party that needs to confirm this action has been authorized.
The problem is, only the user that wants to perform the action will have an iphone (in many cases) and thus the ability to get authorization from our server. The second party does not have access to an internet connection, and will not be able to directly confirm that the first user's request was authorized.
So, my problem is... what sort of system/item could I use to ensure that the second party can confirm that the first party's mobile phone action was authorized by our server?
So far, all of the ideas I have come up with can be subverted by a clever hacker that just duplicates what the second party expects to see as a confirmed request. Things like... giving each second party a unique code that needed to be entered on the first party's mobile app in order to receive confirmation. But the clever user could just create a hacked app that mimics what the real app would do. Obviously, that would be a problem because if the second party believes that the action was authorized when it actually wasn't (due to开发者_StackOverflow hacking), they would lose out on money/time/etc...
Here is a diagram that may make my question a bit clearer:
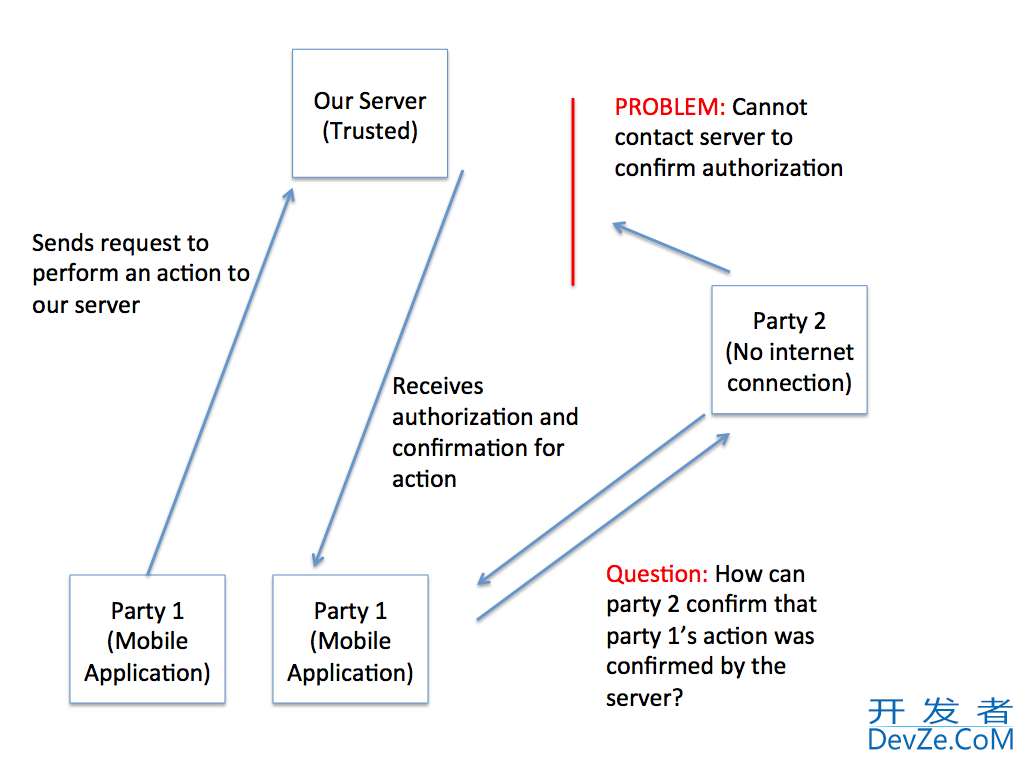
Any ideas would be greatly appreciated.
***Edit: I wanted to add - Party 2 does not have access to a mobile device/computer in some cases, so I need to figure out some piece of hardware that could be deployed cheaply but also perform the role of verification.
If I understand your problem correct; you have a trusted server that can authorize an action for Party 1. That is, the server can decide if Party 1 should be allowed to perform an action. You may call this an authorization service. Party 1 then needs to prove that he was authorized to do this action for Party 2. Party 2 cannot contact the authorization service directly to verify this claim.
The natural solution to this is to let the authorization server issue a digitally signed authorization claim to Party 1. This claim can be i.e. an xml that describes what kind of authorizations Party 1 has. The claim must be digitally signed with a private key that only the authorization server knows. Party 1 recieves this claim from the server and send the claim to Party 2. Party 2 verifies the digital signature using the authorization server's public key. If the digital signature is correct, then Party 2 knows that the claim is valid and what kind of autorizations Party 1 got from the authorization server.
To do this, you must generate a key pair on the authorization server and distribute the public key to each instance of Party 2. This only has to be done once. The public key is not a secret, but it is very important that it is the correct key and that no one with malicious intentions can replace the public key at Party 2 with a fake key.
You will need some kind of device at Party 2 that is able to validate a signed claim. Without that, I don't think this scenario is possible to solve.
 加载中,请稍侯......
加载中,请稍侯......
精彩评论